You can not select more than 25 topics
Topics must start with a letter or number, can include dashes ('-') and can be up to 35 characters long.
|
|
1 year ago | |
|---|---|---|
| forward | 1 year ago | |
| helper | 1 year ago | |
| mirror | 1 year ago | |
| reverse | 1 year ago | |
| .gitignore | 1 year ago | |
| .tool-versions | 1 year ago | |
| LICENSE.md | 5 years ago | |
| README.md | 1 year ago | |
| build-all.sh | 1 year ago | |
| docker-compose.yaml | 1 year ago | |
| down.sh | 1 year ago | |
| dup.sh | 1 year ago | |
| flow.uxf | 1 year ago | |
| overview.png | 5 years ago | |
| overview.uxf | 5 years ago | |
| push.sh | 1 year ago | |
README.md
About
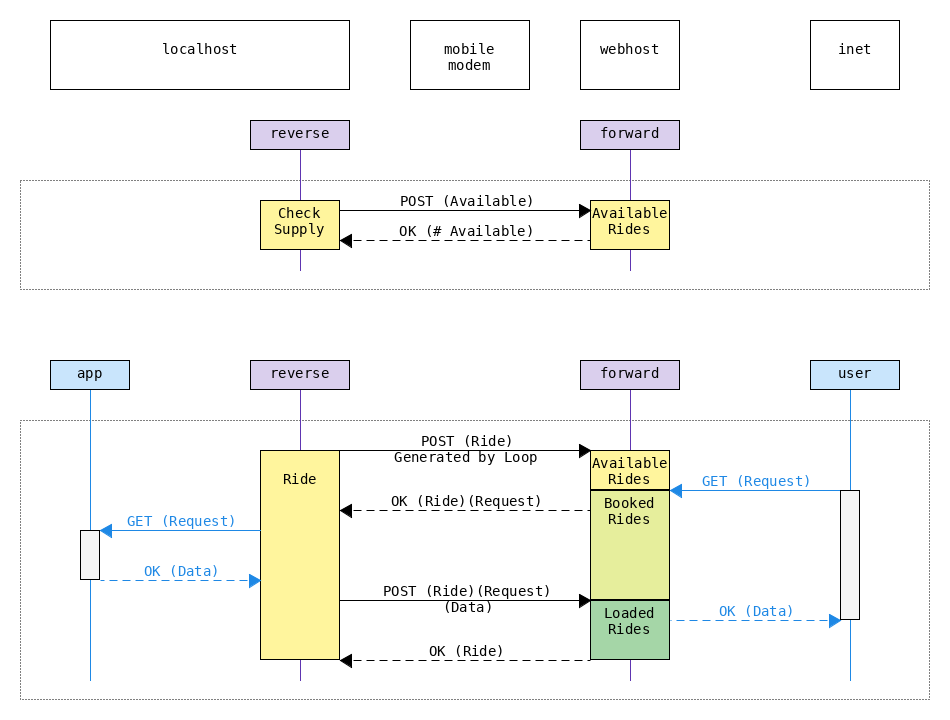
The goal of this project is to bypass the limitations caused by ISPs blocking incoming connections.
To do so, the proxy reverse is created.
reverse sends Ride objects to another proxy, which is called forward.
forward waits for a request from the user,
and inserts the request into the Ride object received form reverse.
The Ride object is then sent back to reverse.
reverse subsequently forwards the request contained in the Ride object to the app.
Upon recieving a reply with data from app, reverse will forward this data to forward,
which in turn will finally forward it to the user.
Control
Routing / Access Control
- currently, there is a 1:1 mapping between
forwardandreverse.- thus any
Ride"submitted" toforwardwill naturally be selected, and circle back toreverse.
- thus any
- thus
forwardandRidecan both be stateless. - if any access control, name resolution, port forwarding were to happen,
it would be done in
reverse.
Overview
What works:
- Forwarding GET requests (including HTTPS).
What does not work:
- Handling 301 (Moved Permanently).
- Forwarding PUT requests - if needed, the logic might be quickly added to
doPutinforward.
Run / Deploy
How to Run / Debug
com.olexyn.misp.embedded.RunAll.main()
How to Deploy
- Set the URIs in code.
- Build (e.g. with
build-install-all.sh) - Put the generated
forward-0.1.warin a servlet container (e.g. Jetty). - Launch the
reverse-0.1.jaron your host.
Security Considerations
- user might access other resources (i.e. another app)
- user might manipulate the
appURL- the URL of the app is provided as ENV
reversecalls said URL.- the URL is never transmitted over the network
- the
Rideobject whichforwardreceives contains only the original request and the response payload fromapp
- user might use redirect magic
- user can not manipulate URL directly
- but if the server is not properly configured, the user might exploit that
- thus only expose local servers that you consider hardened.
- TODO possibly do some Header editing, before calling
appURL inTools.send()
- user might manipulate the
Considerations How to add multiple host mapping
- keep
forwardagnostic- supply parameter to
/indicating desired target service
- supply parameter to
- in
reverse- maintain a map of desired service -> URL